2 weeks ago, Massimiliano Montoro aka Mao, released a new version of Cain & Abel.
Here some of the new features of Cain & Abel v4.9.25:
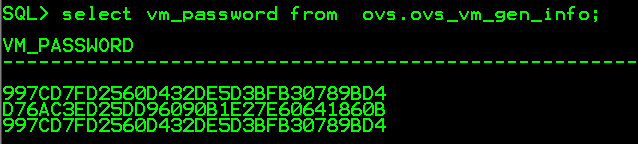
– Oracle 11g (case sensitive) Password Extractor via ODBC.
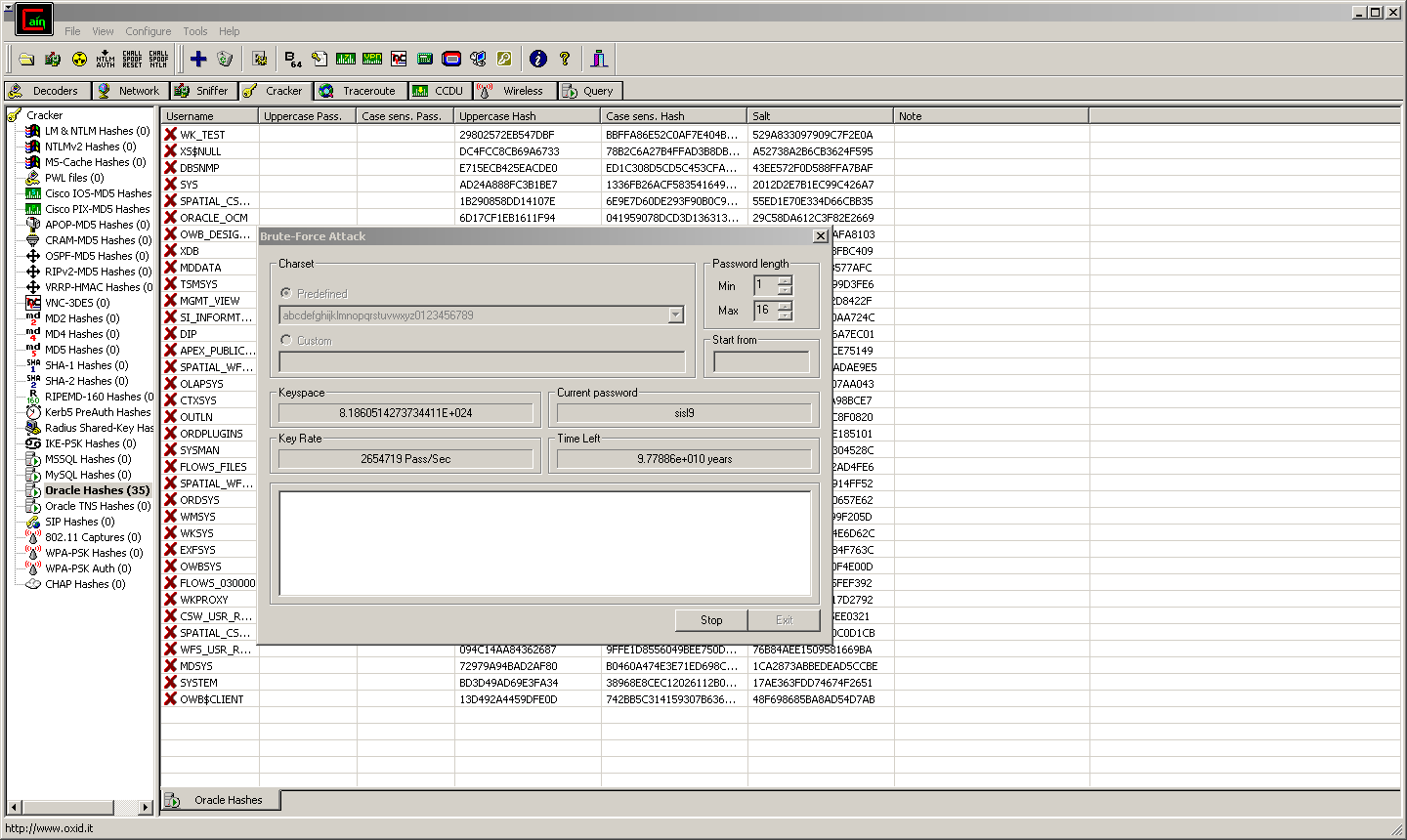
– Added Oracle 11g Password Cracker (Dictionary and Brute-Force Attacks).
– Added support for Oracle TNS 11g (AES-192) in Oracle TNS Hashes Password Cracker.
– Added support for Oracle TNS 11g (AES-192) in Oracle TNS sniffer filter.
– Experimental SQL Query tool via ODBC.
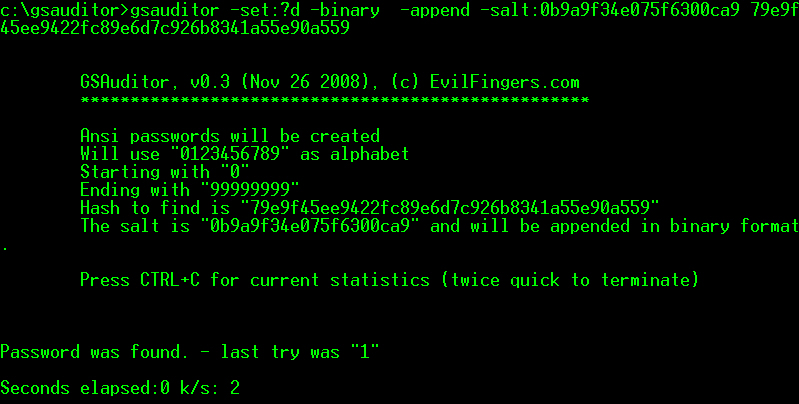
The AES implementation of Cain is slower than the implementation of GSAuditor (6,172,839 vs 2,654,719 on a 2.4 GHz C2D E4600) but 2.6 Million passwords per second (via brute force) is still quite fast.
Massimilano wrote also 3 interesting whitepapers about the TNS authentication based on László Tóth work. Instead of using the oran10.dll/oran11.dll Mao is using the OpenSSL library:
Oracle 9i TNS 3DES authentication details
Oracle 10g TNS AES-128 authentication details
Oracle 11g TNS AES-192 authentication details
 P.S.: This lovely baby is our daughter Anna. Already 10 months old…
P.S.: This lovely baby is our daughter Anna. Already 10 months old…
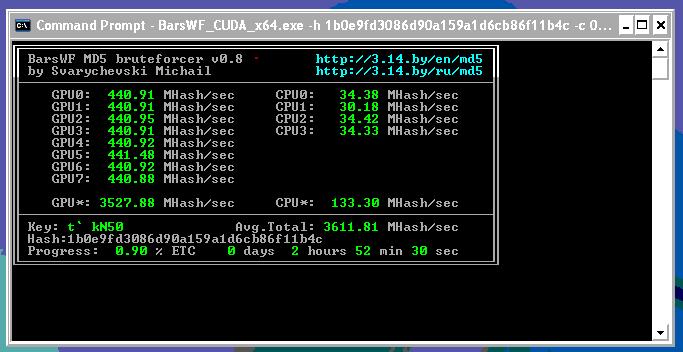 Here are some calculations how long it takes to break MD5 hashes.All passwords (lowercase or uppercase, alpha, 26^1+26^2+26^3+…)
Here are some calculations how long it takes to break MD5 hashes.All passwords (lowercase or uppercase, alpha, 26^1+26^2+26^3+…)