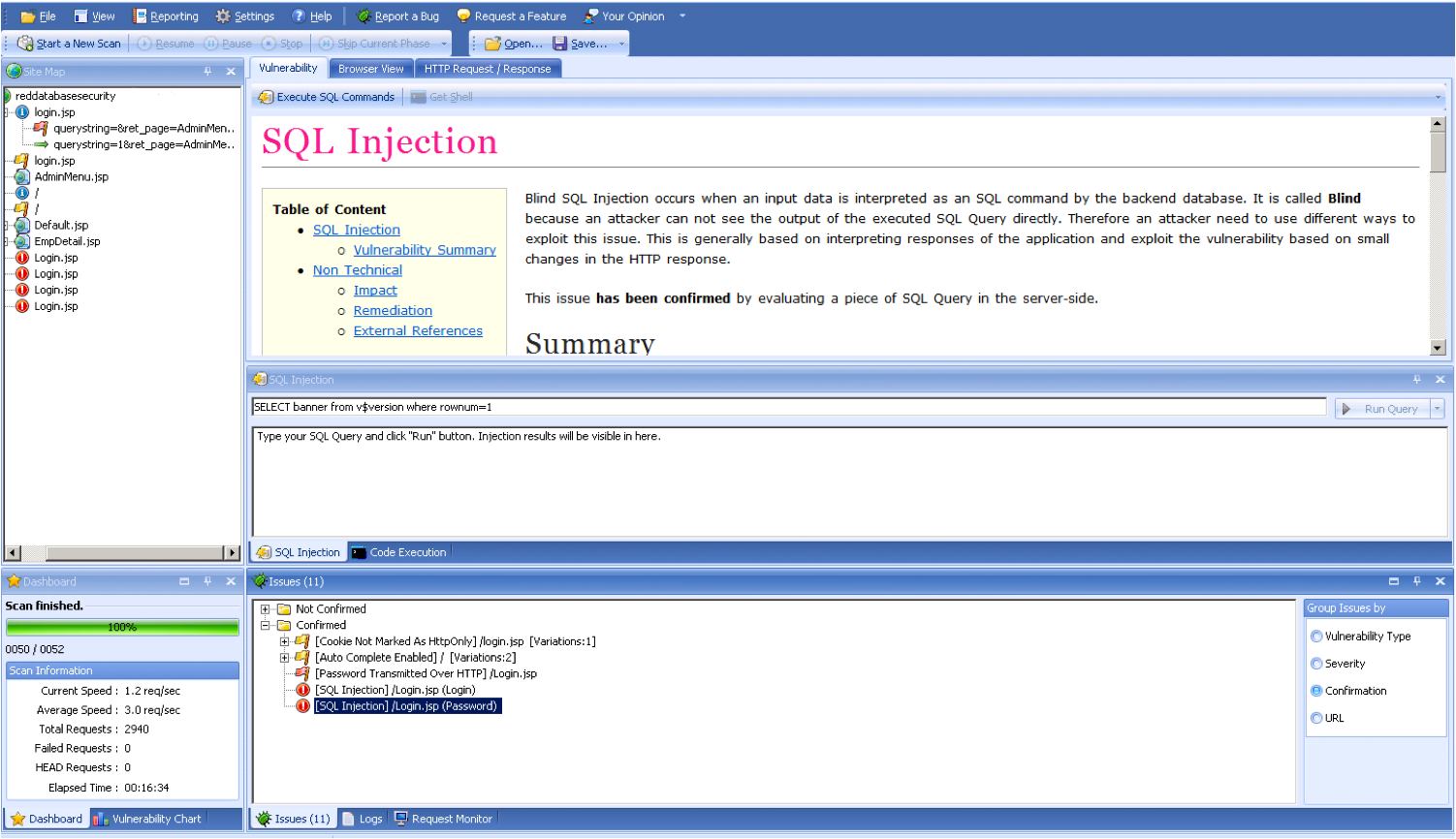
During my research on Russian websites I found a new security tool called „Oracle Security Tools„. This tool offers different methods to exploit Oracle databases.
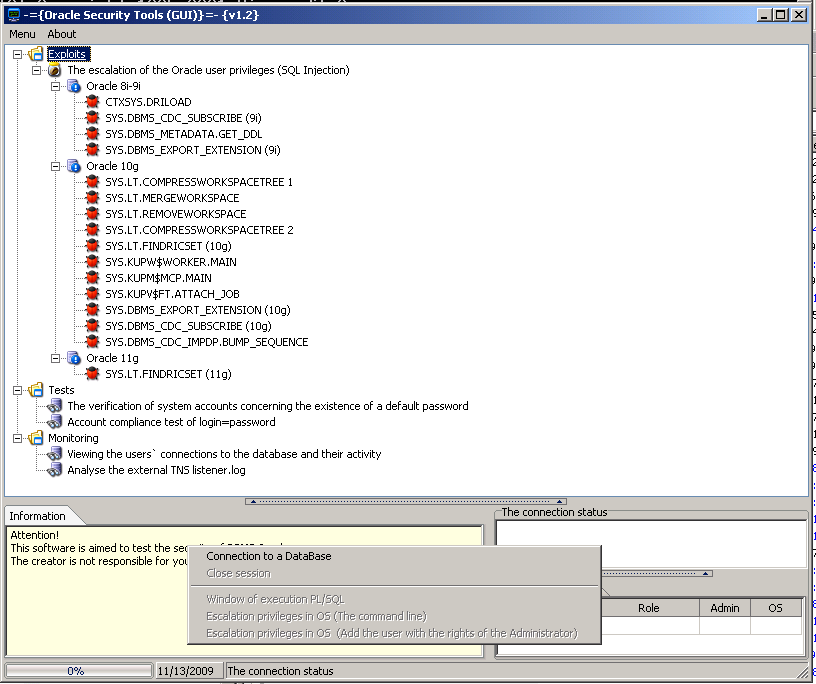
Here is a list of features
- The privileges escalation of the Oracle users;
- The verification of system accounts concerning the existence of a default password;
- Account compliance test of login=password
- The execution of the PL/SQL code;
- The privileges escalation in the OS Windows 2000/XP/2003 (add a local user as root and holder of remote connection powers);
- The infiltration into the OS and the execution of DOS-commands, holding the administrative rights.
- Viewing the users‘ connections to the database and their activity;
- Analyse the external TNS listener.log;
After checking the executable on virustotal I run the program on one of my test VMwares. After switching the russian interface to the english interface I not able to run the tool. I always got the error message:
It seems to be a problem with my vmware system and the mulitple Oracle Homes. After switching to another computer the program was working without problems.