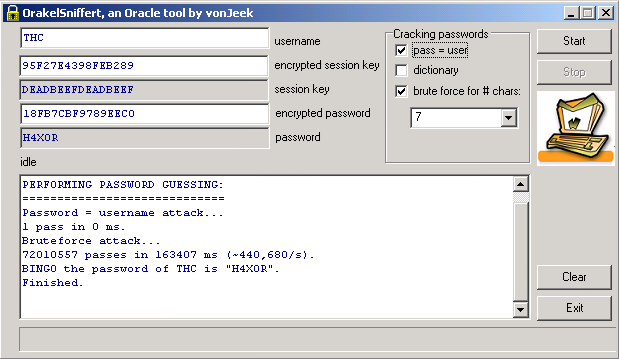
Last week VonJeek from the hacker group THC posted a nice tool and whitepaper
about Oracle Password Security. VonJeek describes how to attack the Oracle password
from sniffed network traffic (USERNAME, SESSION_ENCRYPTED and PASSWORD_ENCRYPTED).
At the moment the THC website is not available.
http://www.thc.org/thc-orakel/
[...]
THC presents a crypto paper analyzing the database authentication mechansim
used by oracle. THC further releases practical tools to sniff and crack the
password of an oracle database within seconds.
[...]
It is a nice paper and THC-Orakel is a nice tool, even if some of the statements
in the paper are not correct (e.g. page 10: "a password must start with a character"
no it can also start with a number or page 13: "The cracking of Oracle passwords
entered a new era after publication of the Oracle password hashing algorithm on
18 October 2005 by the SANS institute" - JoshWright from SANS only collected
public available information like the Oracle Password algorithm and created a summary
paper. The Oracle password algorithm and oracle password tools like checkpwd were
available since years, e.g. here).
This entry was posted on Montag, Juni 4th, 2007 at 17:48 and is filed under Oracle Security. You can follow any responses to this entry through the RSS 2.0 feed.
You can leave a response, or trackback from your own site.
