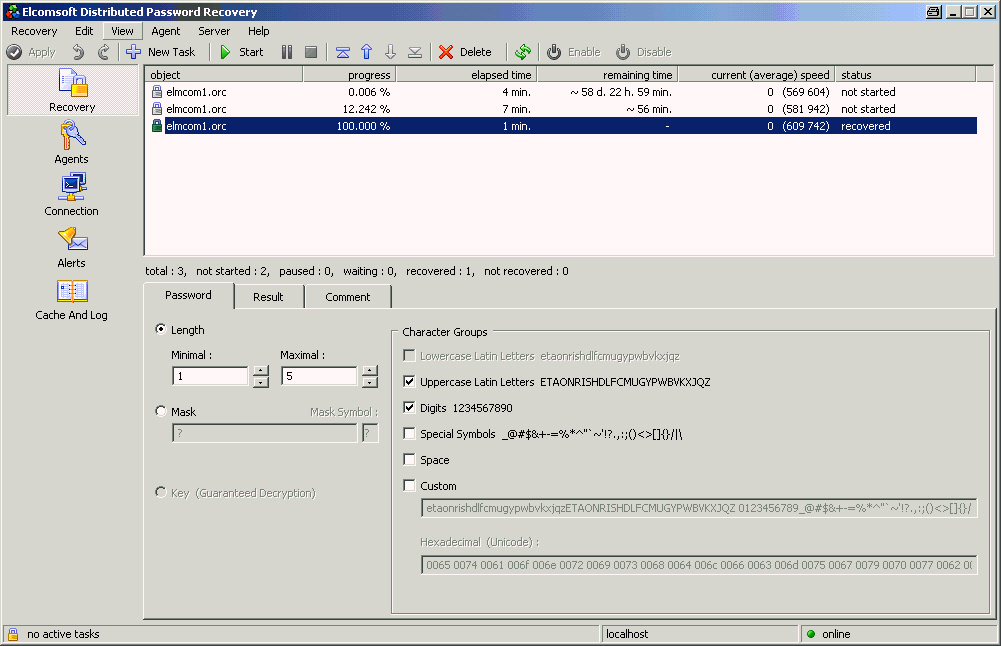
The russian software company Elcom released a new version (2.10.137) of their distributed password cracker.
Woraauthbf (1,480,000 pw/s), orabf (1,110,000 pw/s) and JtR (780,000) in dictionary mode are faster (on my computer) and free.
I was interested to see the performance improvements by using the Geforce graphic card for cracking Oracle passwords but according to the documentation the Geforce 8800 series is only supported for Windows LM/NTLM hashes.
Only bruteforce password cracking for Oracle is supported but I couldn’t find anything in the online help. That’s why I had to play a little bit.EDPR expects the hashes in a file with the extension .orc and username:hash
—– elcom.orc —–
ALEX:5BA465109942B4DE
—– elcom.orc —–
The password cracking itself was simple and I like the possibility to crack passwords in distributed mode on multiple PCs. EDPR is a commercial software and the price starts at 500 USD for up to 20 clients.
I found also a small bug. EDPR is also checking for “ (double-quotes) in passwords. This is not possible in Oracle (afaik, correct me if I’m wrong).