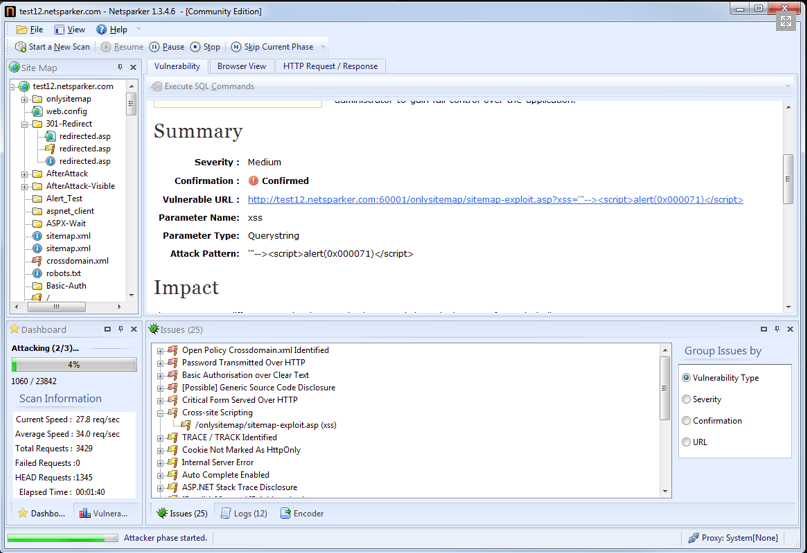
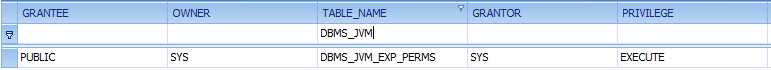
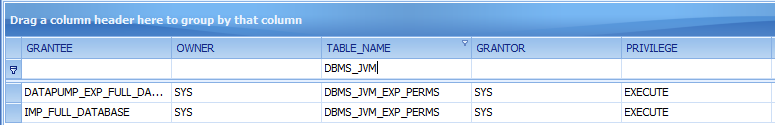
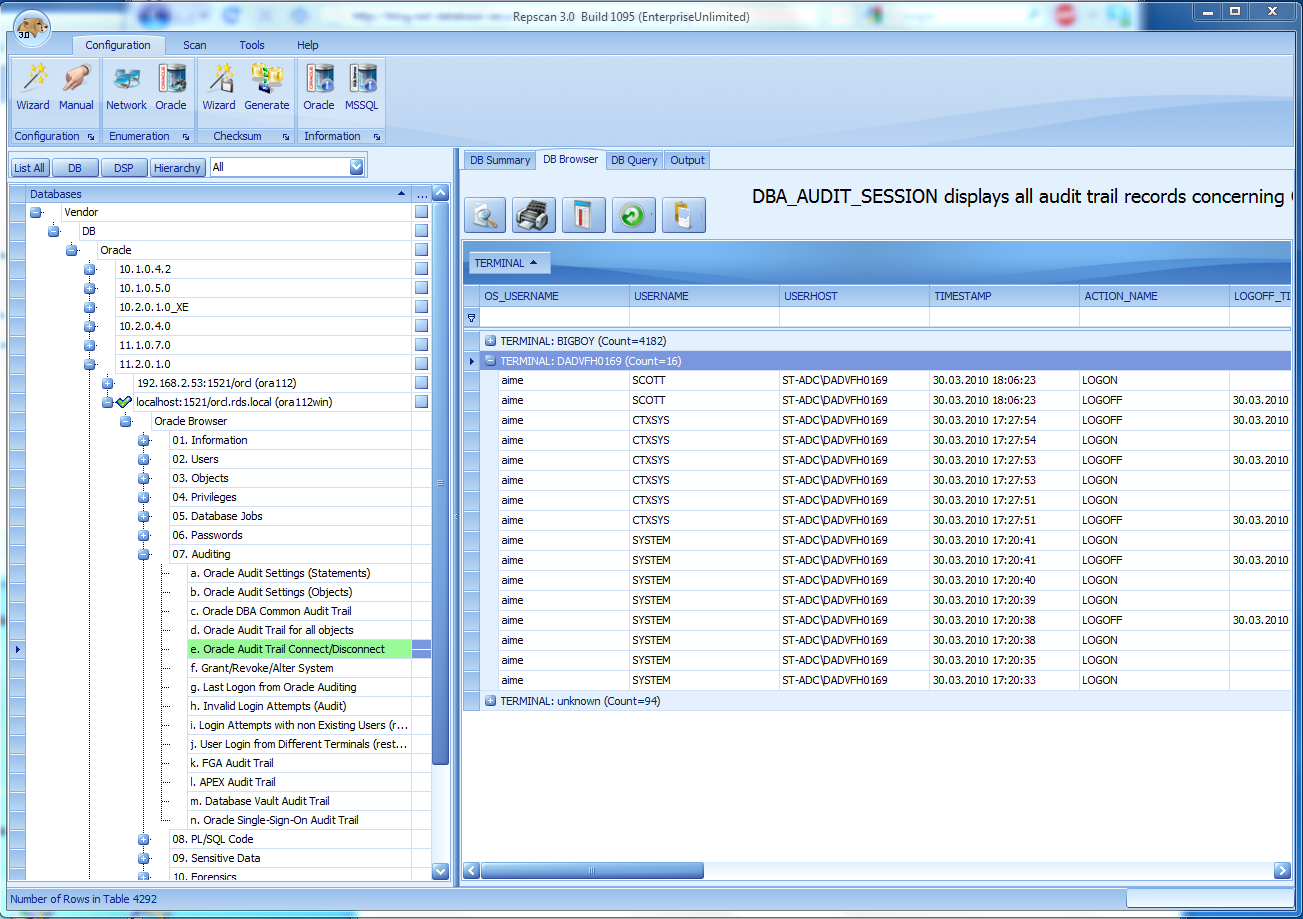
2 days ago I gave a presentation „Oracle 12c from the attackers perspective“ at the DOAG SIG Security. I learned some interesting things, especially that a fix for the Oracle oradebug „disable auditing“ problem is available since 9 months.
Oradebug allows to run OS commands and to enable/disable Oracle SYSDBA and normal auditing on the fly without leaving traces in the audit log. The fix for this problem is available in Oracle 11.2.0.4/12.1.0.1 and was backported to 11.2.0.3 using the patches 15805002, 15808245, 16177780.
By default the setting is not enabled in Oracle 11.2.0.4/12.1..0.1.
The undocumented parameter _fifteenth_spare_parameter (Oracle Description: fifteenth spare parameter – integer – Yeah, really useful) can now disable or limit the oradebug functionality. I could not find any information about this parameter on google or my oracle support.
—— extract from the read me.txt of the patch file——————
## _fifteenth_spare_parameter can be set to „all“, „restricted“ or „none“
## „all“ disables execution of all oradebug commands, „restricted“ disables
## execution of restricted oradebug commands, „none“ (default) allows execution
## of oradebug commands.
—— extract from the read me.txt ——————