At Derbycon 3.0, László Tóth and Ferenc Spala gave a a new presentation „What’s common in Oracle and Samsung? They tried to think differently… “ (Video). The main focus of the presentation was the Samsung encryption and a new framework called sandy but there was also a small Oracle part.
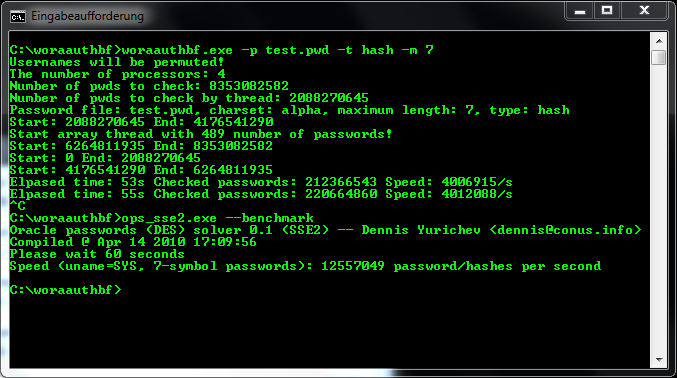
Laszlo and Ferenc showed how to decrypt Oracle database links in Oracle 11.2.0.3 and Oracle 12.1.0.1 using a small utility called „oradecrlink.py“. In previous versions Oracle used DES to encrypt/decrypt database links. These database link passwords start with „05“ (Oracle’s indicator for DES).