Last week at the DOAG conference I published a few numbers about the MD5 cracking speed of BarsWF. Today I found a new record on the web. 3.6 billion (!!!) password hashes per second can calculated with BarsWF. This configuration was using 4x [eVGA 9800GX2] without overclocking.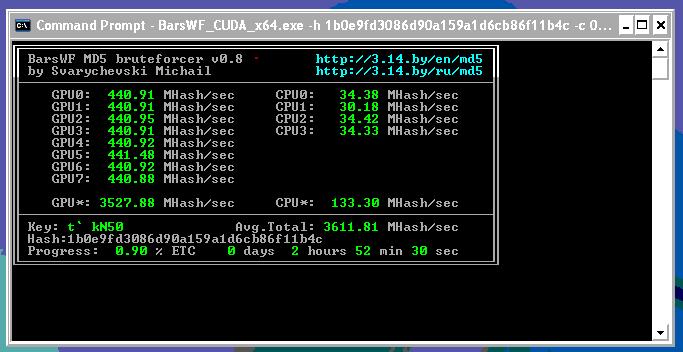 Here are some calculations how long it takes to break MD5 hashes.All passwords (lowercase or uppercase, alpha, 26^1+26^2+26^3+…)
Here are some calculations how long it takes to break MD5 hashes.All passwords (lowercase or uppercase, alpha, 26^1+26^2+26^3+…)
- up to 8 characters => 60 seconds
- up to 9 characters => 26 minutes
- up to 10 characters => 11 hours
All passwords (mixed case, alphanum, 62^1+62^2+62^3+…)
- up to 7 characters => 16 minutes
- up to 8 characters => 17 hours
- up to 9 characters =>44 days
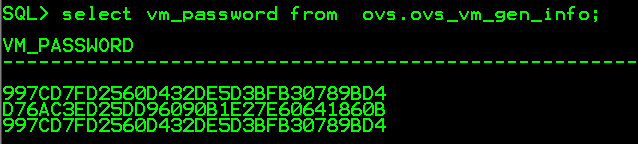
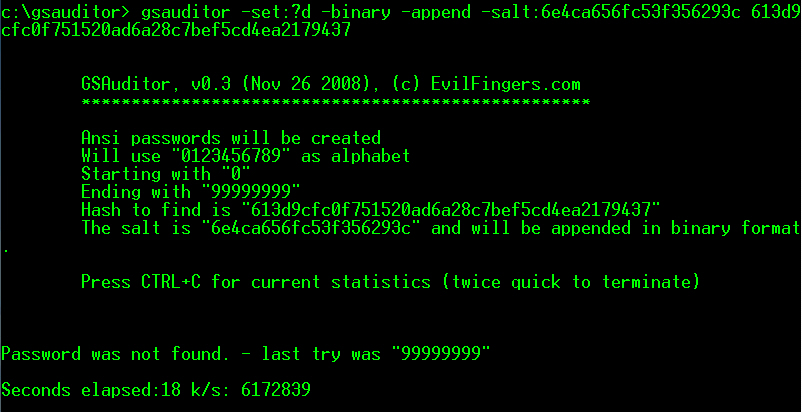
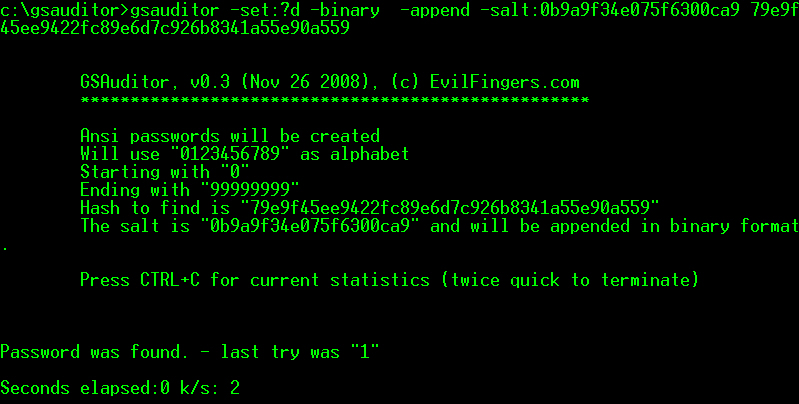
Several Oracle products like OID, OVS (Oracle Virtual Server) or Apex (until 2.2.) are using plain MD5 for hashing passwords. But even the usage of salt (like Apex 3.0) does not help against this computing power….