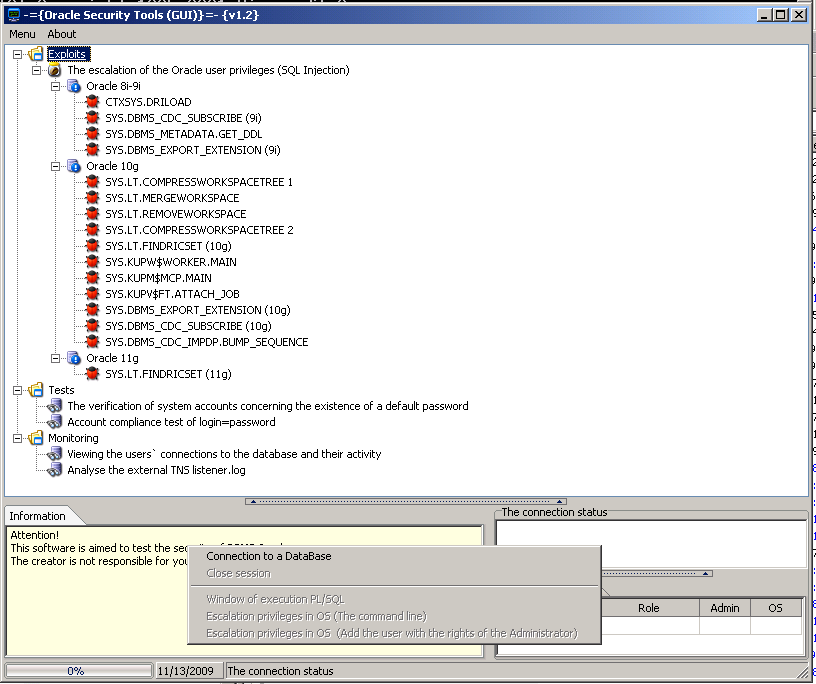
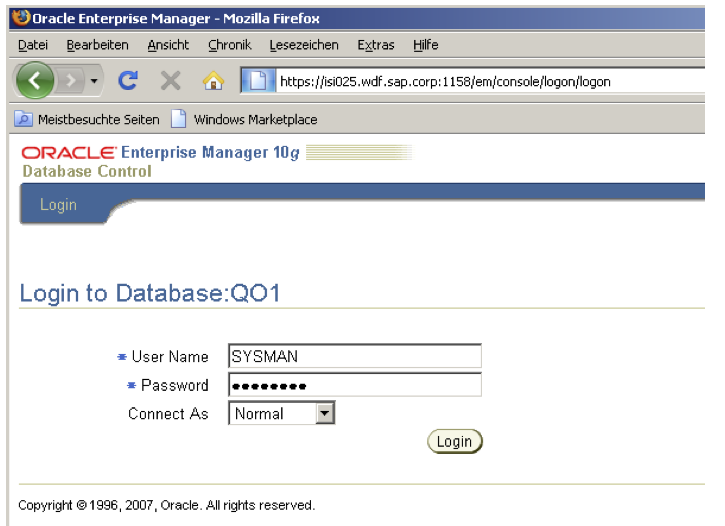
Shaomin Wang from Oracle has posted an interesting blog entry „How Oracle controls access to security vulnerabilities„. There are 3 different access types: Default Access, Global Access and Hierarchical Access.
Depending from the role inside of Oracle (e.g. Global Product Security staff, normal employees or their managers) people have the right to view an individual security bug or all security bugs.
This is a big improvement comparing to the time when I was an Oracle employee several years ago. At that time everybody inside of Oracle had access to security bug information.
The only problem nowadays are security bugs which are not marked as security bugs because Oracle support employees are not aware of the security impact of a normal bug. These bugs are often accessible via MyOracleSupport even for Oracle customers.