Joxean Koreat has released his presentation „Hackproofing Oracle Financials 11i / R12“ from RootedCON 2010. Joxean shows some nice ways to own old and new Oracle Financials installations.
Thanks to Sid for the link via twitter.
Joxean Koreat has released his presentation „Hackproofing Oracle Financials 11i / R12“ from RootedCON 2010. Joxean shows some nice ways to own old and new Oracle Financials installations.
Thanks to Sid for the link via twitter.
This weekend I installed the new version of Oracle 11.2.0.1 (64 bit) for Windows. The 11.2 version for Windows is available since a few days.
I installed the 64 bit version (default installation (next – next – …)) without any problems on Windows 7 system. After that I run a default check with our database scanner Repscan 3 (the most advanced database scanner) against this new database version. According to Repscan this new 11.2.0.1 is no longer vulnerable against the DBMS_JVM_EXP_PERMS exploit and this is correct. Oracle has already fixed the problem. I expect a solution in the upcoming Oracle CPU April 2010.
A quick check in the Repscan database browser shows the difference in the privileges:
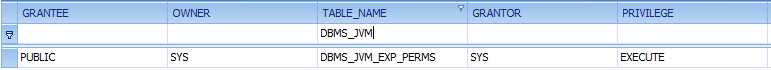
11.2.0.1.0 Linux:
11.2.0.1.0 Windows:
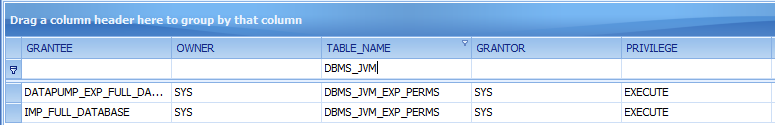
Oracle removed the public privilege from DBMS_JVM_EXP_PERMS and granted privileges to the roles „IMP_FULL_DATABASE“ and „DATAPUMP_EXP_FULL_DATABASE“. The privileges of DBMS_JAVA and DBMS_JAVA_TEST are not modified.
The package DBMS_JVM_EXP_PERMS contains also a bug fix. A comparision between the Windows and Linux version shows the following differencein the package body.
— DBMS_JVM_EXP_PERMS (only in 11.2.0.1 Windows) ——————
[…]
— Check privs
sys.dbms_zhelp_ir.check_sys_priv(DBMS_ZHELP_IR.KZSSTA);
[…]
— DBMS_JVM_EXP_PERMS ——————
After that I analyzed the Oracle database with the Repscan database browser (really useful component, just try the trial version of Repscan) found a few suspicous audit entries in my audit log (sys.aud$).
A user AIME from the terminal „ST-ADC\DADVFH0169“ had a connection to my database?I know that the terminal „ST-ADC\DADVFH0169“ is a terminal somewhere from Oracle. A backdoor in 11.2.0.1? Someone from Oracle was accessing my database?
No. After I checked the timestamp I saw that this entry was created 2 days BEFORE I installed my database. Oracle only forgot to cleanup the audit log before delivering it to customers. If you install Oracle 11.2.0.1 you should truncate the SYS.AUD$ table to avoid questions from (internal/external) auditors.
Paul released a new article about Oracle Java Forensics. He describes how to find traces of Java attacks (e.g. via dbms_jvm_exp_perms) in the Oracle database.
I’ve got some nice ideas from Paul’s article.
Well done.
Microsoft released a patch for CVE-2010-0490. More than 1 year ago I reported this issue to Microsoft.
Finally they fixed the problem.
Bug History:
5-February-2009 – Bug reported to Microsoft Security Response Center
30-March-2010 – Patch for CVE-2010-0490 released
Today Laszlo sent me an email that he published the English version of his Hacktivity 2009 talk „Oracle authentication“ on his webpage. Laszlo was so nice to give me an English private session last year at the Hacktivity in Budapest.
His presentation contains the following topics:
I like the part where Laszlo shows how to hijack an Oracle session.
This presentation is a must for everyone interested in the Oracle authentication process.
Well done Laszlo.