I just uploaded checkpwd 1.23 and sidguess for Mac OSX. The executables are for PPC only because Oracle has only a PPC version of the Oracle Instant Client.
Checkpwd
Sidguess
I just uploaded checkpwd 1.23 and sidguess for Mac OSX. The executables are for PPC only because Oracle has only a PPC version of the Oracle Instant Client.
Checkpwd
Sidguess
During our security training we found an interesting forum entry (CPU Oct 2006 Problem) in Oracle Metalink. It seems that a portscan with nmap on AIX 5.2, OAS 10.1.2.0.2 CPUOCT06 causes a denial of service problem on port 443 (HTTPS). It’s not clear if this problem affects all platforms because nobody answered the forum entry.
Normally it is a good idea to apply CPUs as soon but sometimes new bugs are introduced. Often these problems are specific to a special platform. Another example of a bug which was introduced by the CPUOct2006, CPUJan2007 and CPUApr2007 was a rman problem on Windows 32 bit (Rman fails to restore in 9.2.0.8 with CPU patch installed on Windows platform).
Before applying a patch on a production system you should always perform tests.
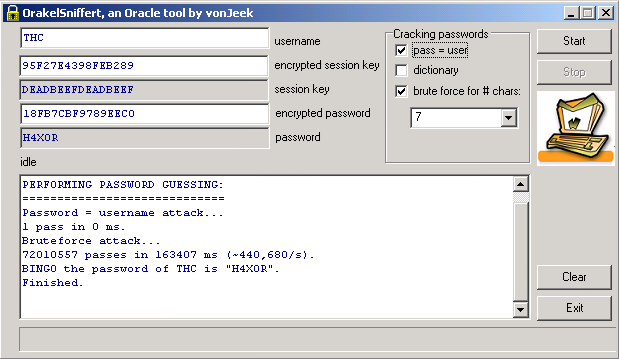
Last week VonJeek from the hacker group THC posted a nice tool and whitepaper about Oracle Password Security. VonJeek describes how to attack the Oracle password from sniffed network traffic (USERNAME, SESSION_ENCRYPTED and PASSWORD_ENCRYPTED).
At the moment the THC website is not available. http://www.thc.org/thc-orakel/
[...]
THC presents a crypto paper analyzing the database authentication mechansim used by oracle. THC further releases practical tools to sniff and crack the password of an oracle database within seconds.
[...]
It is a nice paper and THC-Orakel is a nice tool, even if some of the statements in the paper are not correct (e.g. page 10: "a password must start with a character" no it can also start with a number or page 13: "The cracking of Oracle passwords entered a new era after publication of the Oracle password hashing algorithm on 18 October 2005 by the SANS institute" - JoshWright from SANS only collected public available information like the Oracle Password algorithm and created a summary paper. The Oracle password algorithm and oracle password tools like checkpwd were available since years, e.g. here).
The following link contains a podcast where David talks about database forensics.
On the AusCERT2007 conference David Litchfield said that he start the research on a new project called FEDS (Forensic Examiners‘ Database Scalpel).
More information here