Yesterday, Dennis Yurichev has published details about his FPGA based Oracle (DES) password cracker. His cracker can check up to 60 Mill. passwords per seconds (for short usernames) in brute force mode.
This is a good opportunity to show the current status of Oracle Password Cracking.
The benchmark numbers on our website are a little bit outdated and I will refresh them soon.
Here a quick summary of the fastest programs in every class (AFAIK, please correct me if you know
faster tools). All tests were performed on my old Core2Quad 2.4 GHz.
New Intel i7 would perform much faster (30-50%) comparing to Core2Quad.
If you look for pure numbers, dictionary based rainbow tables for DES are the fastest solution with approx. 250 Mill password hashes, followed by FPA with 60 Mill pw/sec, followed by brute force with 4 Mill pw/sec.
The SHA1 algorithm is a bad choice from the password cracking perspective because it can be cracked much faster (30 Mill pw/s instead of 4 Mill pw/s) on the same computer.
1. Dictionary Based (* Core2Quad 2.4 GHz)
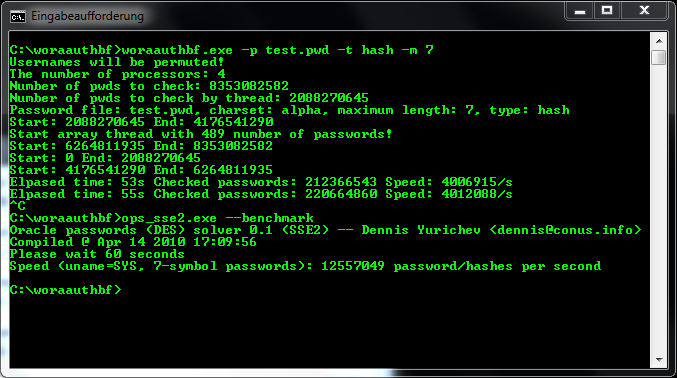
DES: approx. 3 Mill pw/sec (Repscan 3.0 and woraauthbf)
SHA1: approx. 19 Mill pw/sec (Repscan 3.0)
2. Brute Force (* Core2Quad 2.4 GHz)
DES: up to 4 Mill pw/sec (Repscan 3.0 and woraauthbf)
SHA1: approx. 30 Mill pw/sec (Repscan 3.0)
3. Rainbow Table (* Core2Quad 2.4 GHz)
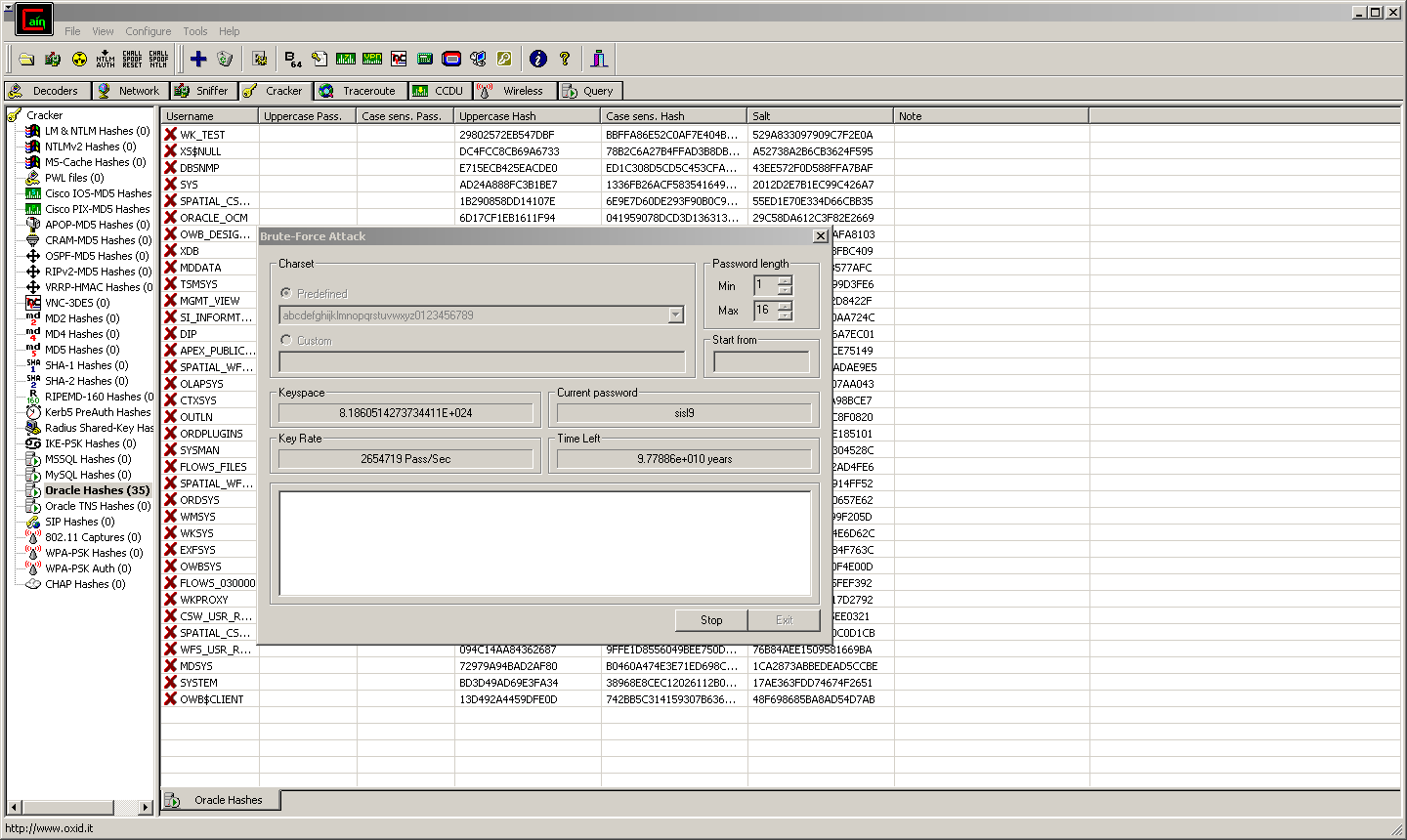
DES: n/a (Cain)
SHA1: hash salted, not useful
4. Dictionary based Rainbow Tables (* Core2Quad 2.4 GHz)
DES: up to 250 Mill pw/sec (ophcrack)
SHA1: hash salted, not useful
5. FPGA
DES: up to 60 Mill pw/sec (Dennis Yurichev)
SHA1: not available
6. GPCPU
DES: n/a
SHA1: n/a (estimated 175 Mill pw/sec)