Oracle just released the January 2009 CPU.
The database part of this CPU contains fixes for 10 vulnerabilities in the Oracle database. This time Oracle fixed 3 of our vulnerabilities (2 in the database) and 1 in JDeveloper (reported 2005, CVE-2008-2623).
15 researchers are mentioned in this report (2 from Red-Database Security (Franz Hüll and I). The usual suspect (Esteban, Joxean and David) are part of the reporters too.
The most critical bug (CVE-2008-5437) allows any user with execute privileges on dbms_ijob (e.g. DBA or hacker/user with DBA privs) to bypass Oracle Auditing completely. This means no traces in the AUD$ and/or the operating system! All databases are affected.
Before I will release details for this issue I must check the patches from Oracle what bug Oracle has fixed. I reported 2 different bugs to Oracle where you can bypass Auditing. The exploit and idea for one of the bugs came from my former Oracle colleague Volker Solinus.
The second bug from us is a SQL injection bug in DBMS_STREAMS_AUTH (CVE-2008-4015). Here it is possible to become DBA.
More details within the next days.
 P.S.: This lovely baby is our daughter Anna. Already 10 months old…
P.S.: This lovely baby is our daughter Anna. Already 10 months old…
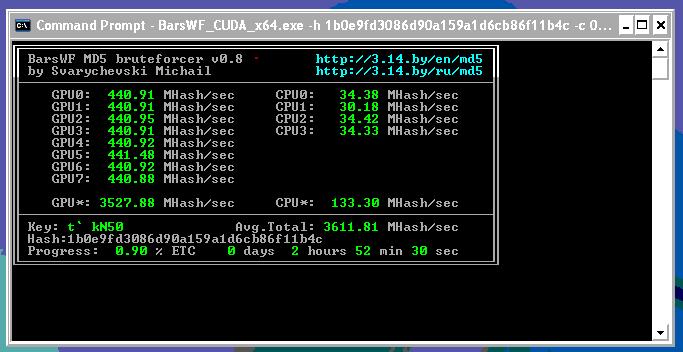 Here are some calculations how long it takes to break MD5 hashes.All passwords (lowercase or uppercase, alpha, 26^1+26^2+26^3+…)
Here are some calculations how long it takes to break MD5 hashes.All passwords (lowercase or uppercase, alpha, 26^1+26^2+26^3+…)